- How Secure Is Your Private Information Online?
- What Is Digital Privacy?
- How to Protect Yourself on the Internet
- Tweak Your System’s Security Settings
- Use Strong, Unique Passwords
- Enable Two-factor Authentication
- Delete Unused Apps And Browser Extensions
- Block Search Engines From Tracking You
- Browse Online With a Secure Virtual Private Network (VPN)
- Update Your Software Regularly
- Block Targeted Ads And Data Tracking
- Encrypt Your Data to Prevent Unauthorized Access
- Remove Unnecessary Third-party App Connections
- Be Cautious About What You Share Online
- Conclusion
- FAQ
How Secure Is Your Private Information Online?
If you are anxious about your security on the Internet, you have every cause for worry. In todays’ turbulent world, digital privacy is becoming more of a concern. The number of data compromises is on the rise, so it’s no wonder seven in ten users take online privacy measures.
Every time you go online, you dive into dangerous waters, so it is essential that you know how to protect your data. Here are some of the most common Internet privacy issues users face in this day and age:
- Data Breaches: Unauthorized individuals can gain access to your sensitive information and use it for criminal purposes.
- Online Surveillance: Governments, corporations, and other entities can compromise your online privacy and security by monitoring your online behavior and communications.
- Scams and Phishing: Criminals may use deceptive tactics to trick you into disclosing sensitive information, such as your credit card details or passwords.
- Tracking and Profiling: Businesses and organizations can use cookies and other tracking technologies to monitor your online behavior and throw targeted ads at you.
- Insecure Wi-Fi Networks: Hackers may intercept the data you transmit using public Wi-Fi networks.
- Internet of Things (IoT) Vulnerabilities: IoT systems can be hacked by criminals to access your personal details or control connected devices.
- Lack of Transparency: Online platforms and services often design complicated terms of service. As a result, it may be difficult to understand how your personal data is being used or shared.
When using the Internet, you need to be cautious about online privacy. The web is swarming with nefarious activities, and criminals can gain unauthorized access to your sensitive information, which may lead to identity theft, fraud, and other negative outcomes.
What Is Digital Privacy?
With all the cautions highlighted above, you might be wondering, what is Internet privacy? A long story short, digital privacy is the protection and control of personal information used, shared, and stored in digital environments. It involves the right of individuals to decide how their data is collected, utilized, and transmitted in an increasingly interconnected digital world.
Online privacy empowers you to maintain control over your personal details, like your name, address, and financial information, ensuring that they are not accessed or exploited without your explicit consent. It involves various strategies and measures, such as implementing strong encryption or using protected connections.
Unfortunately, despite digital privacy protection efforts and initiatives, Internet privacy issues and challenges persist in the modern world. With rapid technological advancements, there are more and more avenues for potential data breaches, and individuals’ right to online privacy is often at risk.
How to Protect Yourself on the Internet
So, what is the best way to protect your personal information in the digital realm? To ensure your personal data is handled responsibly and securely, you need to navigate the Internet with digital privacy in mind.
Still wondering, what is digital privacy in the field? Here is how to protect your devices from cybersecurity threats and get the most out of your online experience using the best digital privacy practices:
Tweak Your System’s Security Settings
First and foremost, you need to make sure your system is configured to keep security threats at bay. Windows 10 contains multiple security mechanisms, so we recommend you to enable the best protection measures on your PC.
If tweaking numerous security settings seems a daunting task to you, we recommend using dedicated digital privacy protection software. For instance, you can employ Auslogics BoostSpeed to get the job done.
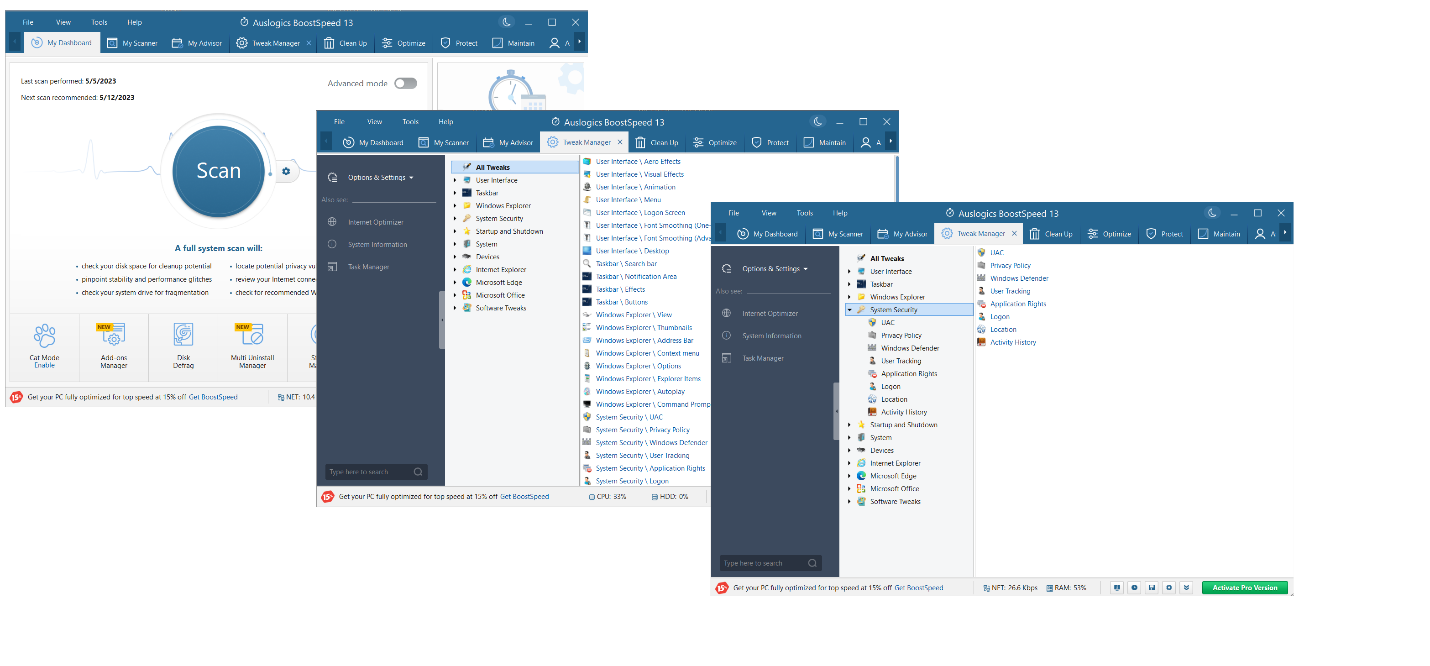
Auslogics BoostSpeed is a PC optimization app that has various helpful features in its arsenal, including Tweak Manager – a powerful tool capable of tuning up your Windows OS. With Tweak Manager, you can configure your user interface, taskbar, Windows Explorer, startup and shutdown, system, device, browser, and app settings. Last but not least, the tool lets you enhance your online privacy and security.
Here is how to protect your personal information against Internet privacy issues with Auslogics BoostSpeed’s Tweak Manager:
- Download and install the Auslogics BoostSpeed software on your Windows PC.
- Go to the Tools tab, expand the System Tools option and click on Tweak Manager.
- Enter the System Security category. It allows you to configure your UAC, Windows Defender, privacy policy, user tracking, application right, logon, location, and activity history settings to improve your digital privacy.
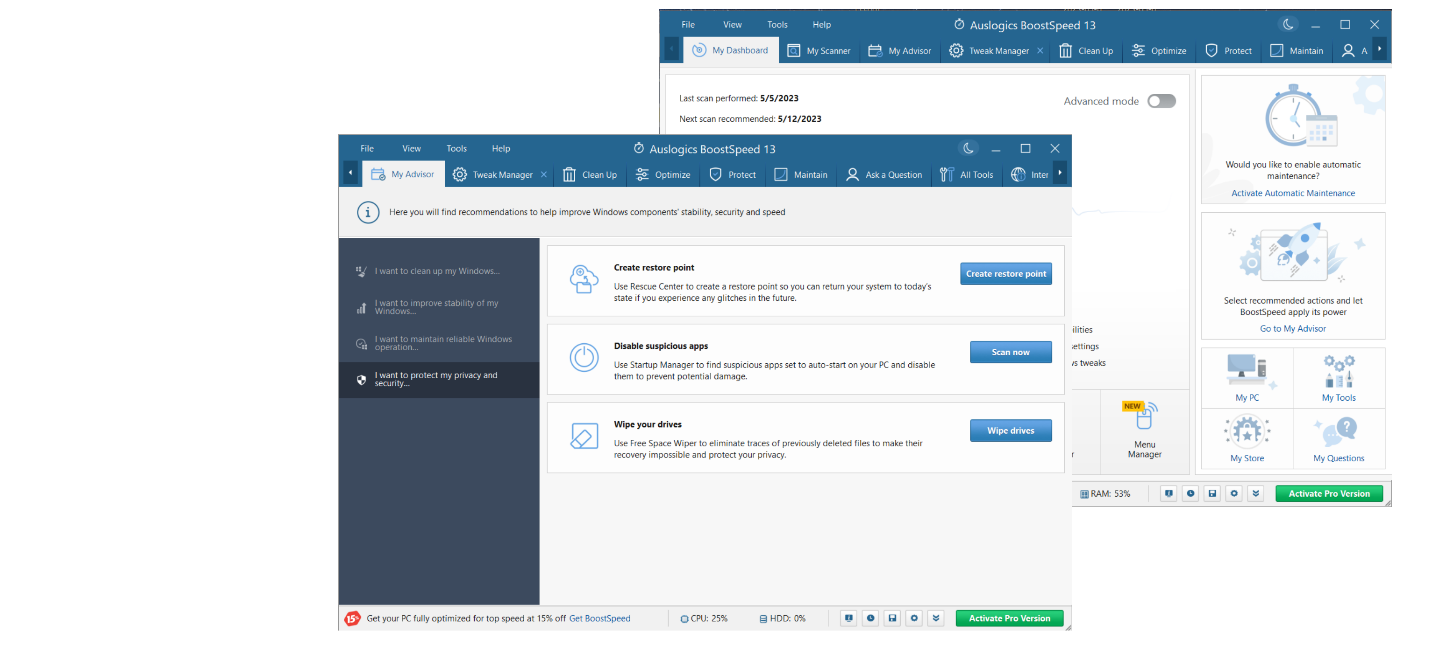
Auslogics BoostSpeed offers another tool designed to boost your security on the Internet. It is called My Advisor and contains recommendations on how to improve your system’s speed, stability and security. Here is how to enhance online privacy and security with Auslogics BoostSpeed’s My Advisor:
- Fire up the Auslogics BoostSpeed software.
- Click the Go to My Advisor link on the right.
- On the left pane, go to the I want to protect my privacy and security section.
- Now you can create a restore point to back up your data, scan your system for suspicious apps and eradicate the traces of previously deleted files. Taking these measures will make your computer more secure.
Use Strong, Unique Passwords
Weak passwords are easy to guess or crack, especially for experienced hackers or dedicated software, which makes your accounts vulnerable to hacking attempts. Besides, using the same password for multiple accounts puts your privacy at risk: if one of your accounts gets hacked, the attacker will easily gain access to all the other accounts with the same password.
Creating strong and unique passwords for your accounts is essential for reducing the risk of unauthorized entry. It is important that you use complex passwords that include a unique mix of upper and lower case letters, numbers, and special characters. Also, make sure you save your passwords securely.
Enable Two-factor Authentication
Setting up two-factor authentication for your accounts will add an extra layer of security to your accounts. It will require additional verification, such as a unique code or a biometric verification, beyond just a username and password. With two-factor authentication in place, attackers will find it much more difficult to gain unauthorized access to your accounts.
Delete Unused Apps And Browser Extensions
Deleting unused apps and browser extensions enhances digital privacy by minimizing data exposure, reducing tracking and profiling, and patching potential entry points for security breaches.
Since managing permissions and privacy settings across numerous apps and extensions can be challenging, you can uninstall some programs to make your system lighter and streamline the process of privacy management by removing unneeded items. This way, you will find it easier to maintain control over your data.
Block Search Engines From Tracking You
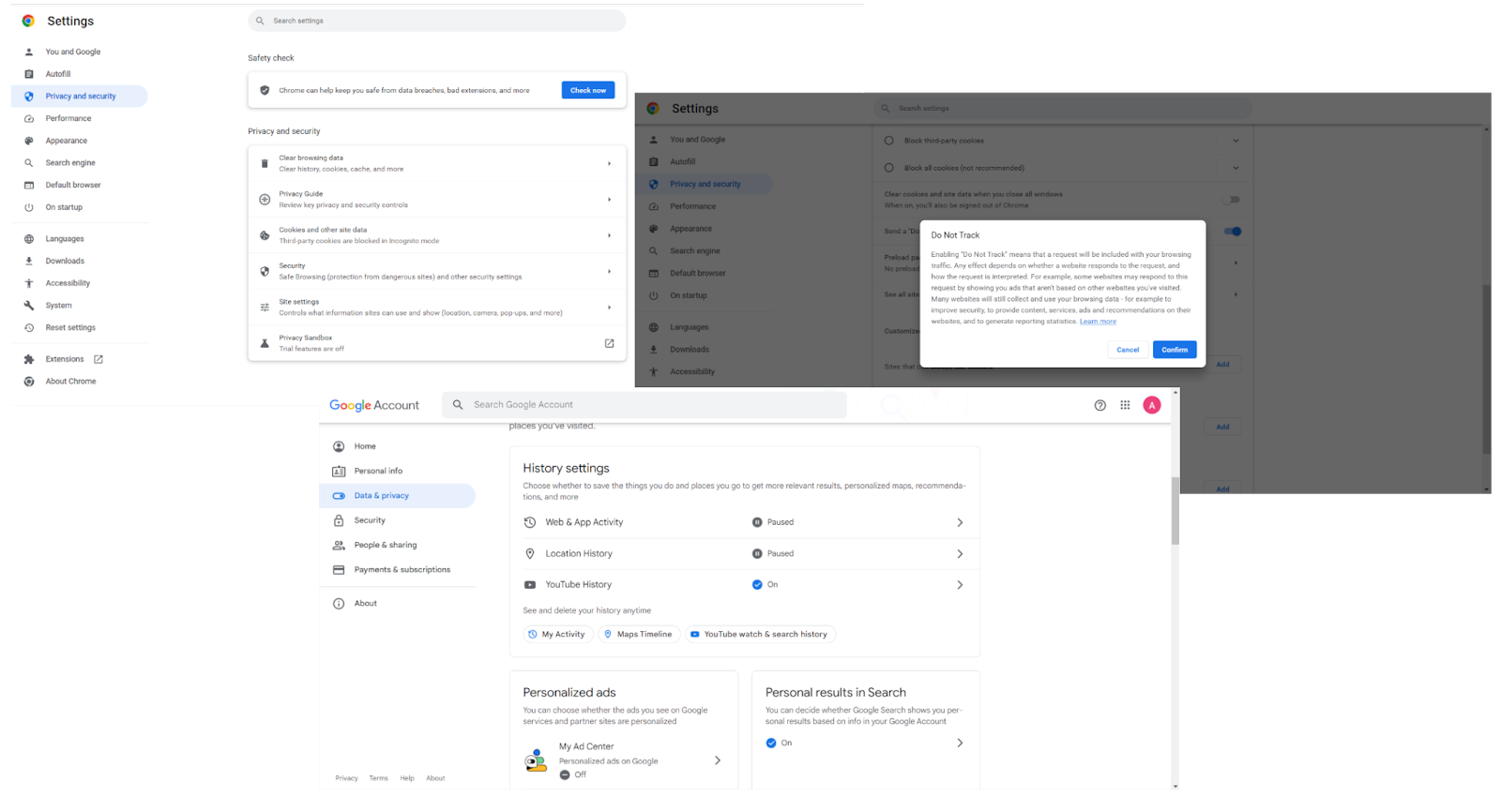
To increase your security on the Internet, we recommend blocking search engine tracking. This will reduce the amount of personal data collected by search engines, like Google, about your online activities. As a result, you will be able to avoid personalized search results and targeted ads and hide your sensitive details. Here is how to prevent Google and the websites you access through it from tracking you:
- Fire up the Google browser.
- Navigate to the top-right corner, click “More,” and select “Settings.”
- Go to Privacy and security and then click “Cookies and other site data.”
- Switch the toggle next to Send a “Do not track” request with your browsing traffic to On.
- Then click on your Google account icon and select “Manage your Google account.”
- Expand the Data & privacy section and go to “Things you’ve done and places you’ve been.”
- In this section, you can configure your digital privacy policies, such as your history settings, personalized ads and search results, and data sharing.
Browse Online With a Secure Virtual Private Network (VPN)
There are several reasons to start using a VPN as soon as possible, boosting your digital privacy being the most crucial one. Browsing with a reliable VPN offers significant advantages and benefits, such as traffic encryption, security on public Wi-Fi, access to restricted content, and protection in high-risk environments.
The most important thing is that a VPN can hide your real IP address and route your Internet traffic through a server located in a different geographic location. This provides anonymity, making it challenging for entities and individuals to track your online behavior or trace your activities back to your real identity.
Also Read: How to choose VPN: Best Free VPN for Windows 10 PC
Update Your Software Regularly
Keeping software up to date is essential for improving Internet security and online privacy. Software updates often deliver patches that fix known security vulnerabilities and weaknesses. By regularly updating your apps, you apply the latest security measures, reduce the risk of exploitation by cybercriminals and safeguard your system against data breaches.
Besides, it is vital that you know how to update drivers on a Windows 10 PC. Outdated drivers can be exploited by criminals to inject malware into your system, so make sure to stay current with driver updates.
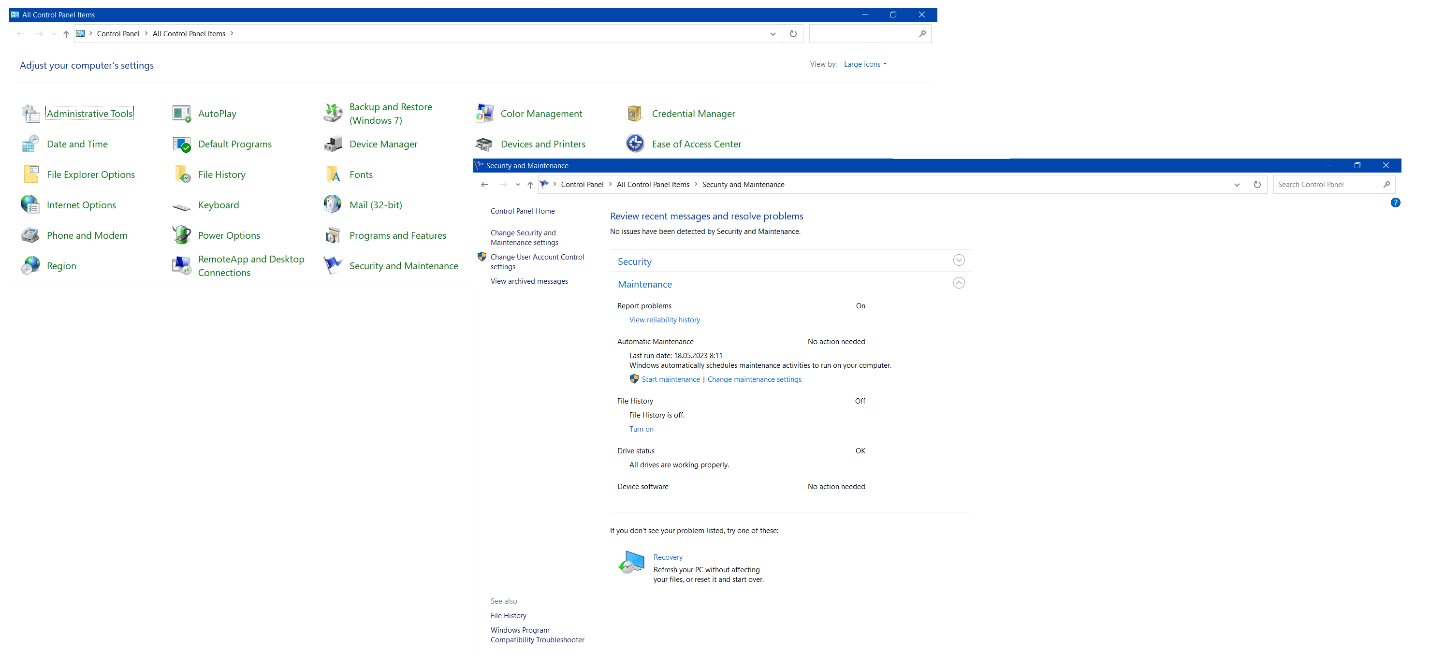
Another tip on how to protect your data is to configure Windows automatic maintenance. For this, you can use the built-in Windows Automatic Maintenance feature: Control Panel -> Security and Maintenance -> Maintenance -> Automatic Maintenance. It will perform automated maintenance activities and resolve security problems.
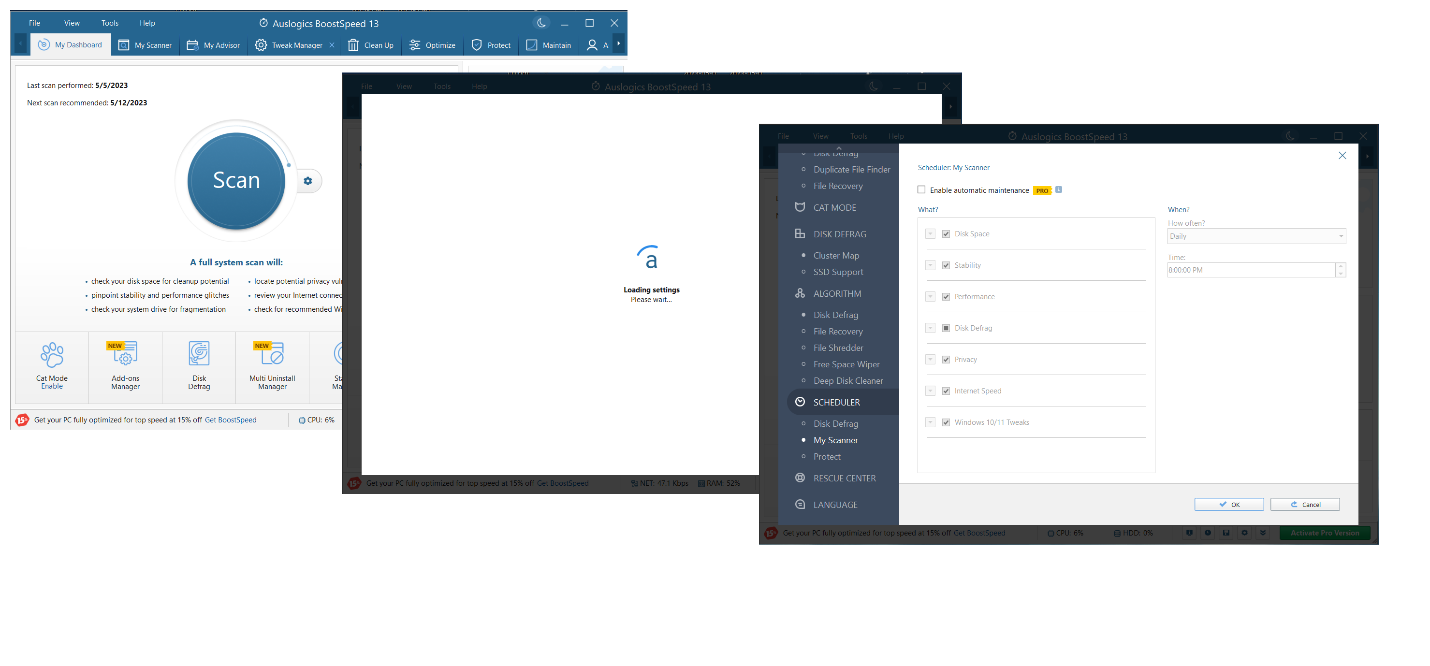
Alternatively, you can utilize Auslogics BoostSpeed’s My Scanner feature. It will conduct automated system check-ups and troubleshoot problems, including Internet privacy issues, on your PC at a convenient time:
- Download and install Auslogics BoostSpeed.
- Click on File and select Settings.
- On the left pane, navigate to Scheduler and click “My Scanner.”
- Check “Enable automatic maintenance.”
Block Targeted Ads And Data Tracking
By turning off tracking, you limit the amount of your personal data available to advertisers. This, in turn, reduces the risk of your details being stolen, sold, misused, or targeted in cyberattacks.
Keep in mind that while personalized ads may seem convenient, they are based on monitoring and analyzing your online behavior. Keeping targeted ads at bay will help you maintain a greater level of digital privacy.
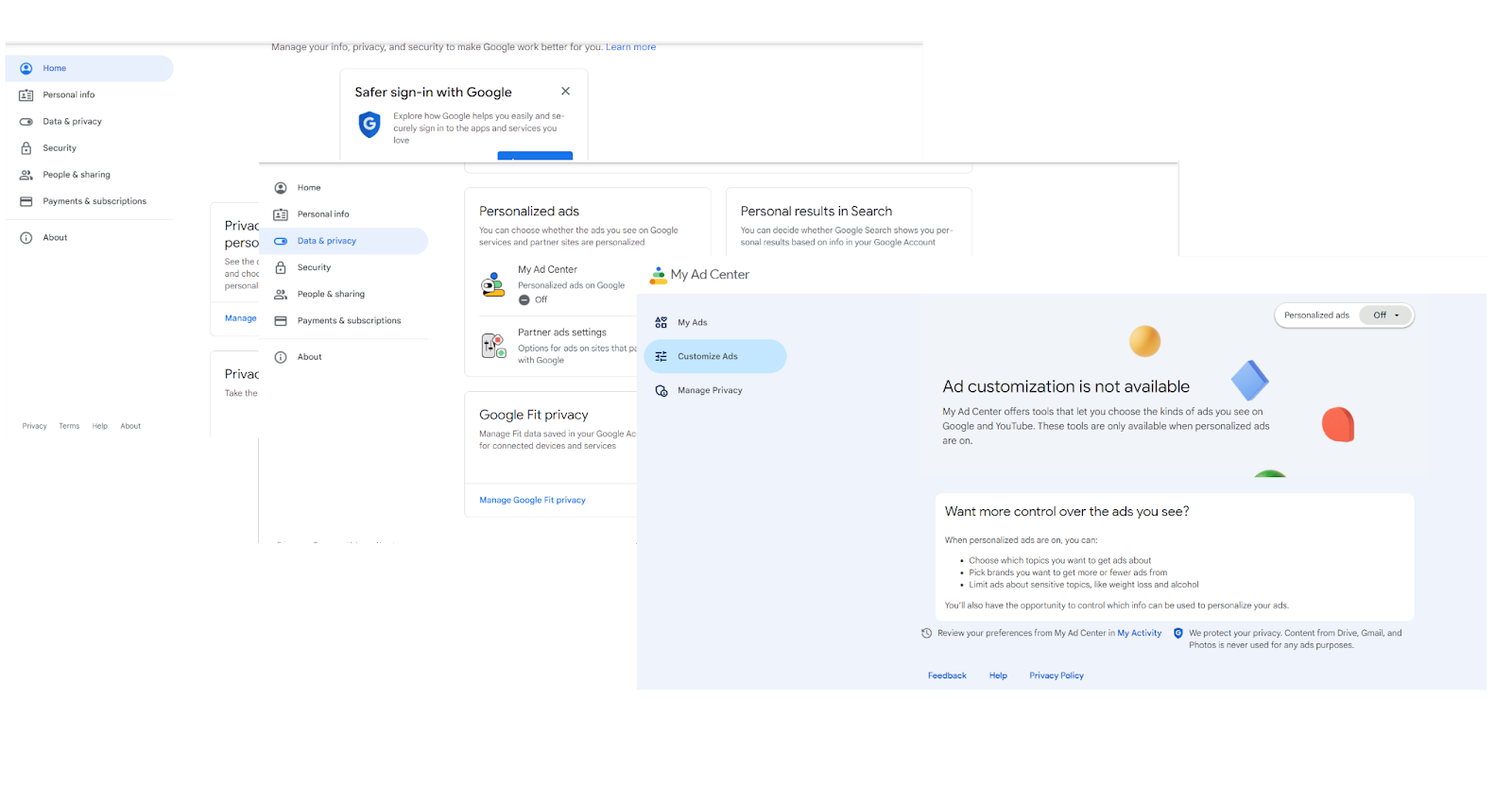
Adjusting your browser’s settings can help you disable data tracking and block targeted ads. Here is how you can do that in Google:
- Log into your Google account.
- Click on “Manage your data & privacy” or enter the Data & privacy section through the left pane.
- Navigate to the “Personalized ads section” and click on “My Ad Center.”
- Switch the toggle next to “Personalized ads” to Off.
Alternatively, you can install privacy-focused browser extensions, tweak privacy settings on websites and apps, or use a VPN to hide your online activities.
Encrypt Your Data to Prevent Unauthorized Access
Encryption may be the best answer to how to protect your data. Otherwise, if intercepted during transmission, it can be easily exploited by unauthorized users. By using complex algorithms, encryption converts your data into an unreadable format, making it meaningless to anyone not having the encryption key.
To keep your personal information safe, you need to apply reliable encryption methods and store encryption keys securely. There are various ways you can encrypt files and folders in Windows 10 – you just need to find the right option for your digital privacy purposes.
Remove Unnecessary Third-party App Connections
By reducing the number of app connections on your computer, you get to expose less data to third-party developers. Consequently, there is less risk of your personal information being shared with or sold to other parties without your knowledge or explicit consent.
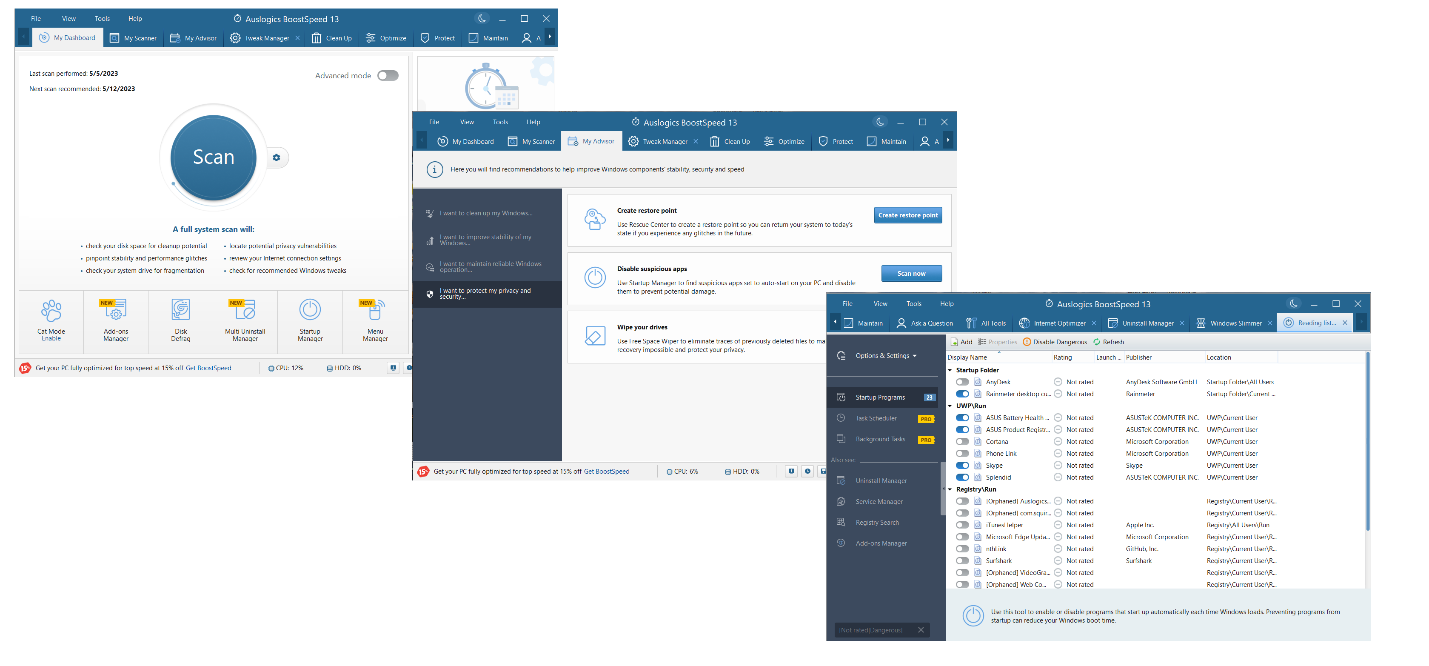
You can disable unneeded, rarely used or suspicious apps using Auslogics BoostSpeed’s My Advisor feature:
- Download and install the Auslogics BoostSpeed app.
- Click on the Go to My Advisor link.
- In the My Advisor tab, click on I want to protect my privacy and security.
- Navigate to the Disable suspicious apps option and click on Scan now.
- If the tool detects potentially dangerous or suspicious programs, make sure to disable them.
Be Cautious About What You Share Online
Being careless about what personal information is visible to others increases the risk of Internet privacy issues.
For instance, if information like your full name, location, phone number, and frequently visited places gets into the wrong hands, ugly consequences like harassment or stalking may occur. Fortunately, you can control who can see your posts, pictures and personal details on social media. By keeping this kind of information private, you reduce the likelihood of falling victim to criminal activities.
Conclusion
So, what is privacy on the Internet? In general, digital privacy refers to measures related to the protection of personal information and concerns about potential threats to individuals and organizations’ data in the digital realm. The fundamental principle on which digital privacy is based is one’s right to control their personal information and how it is used, stored, and shared online.
From identity theft to digital spying to online harassment, digital crime abounds. Thus, if you are wondering how to protect your personal information, you can take measures such as
- configuring your system’s security settings,
- setting up strong passwords,
- enabling two-factor authentication,
- protecting your online accounts,
- using VPNs,
- updating your software regularly, and
- blocking targeted ads, among other things.
FAQ
Why Is It Important to Keep Personal Information Private Online?
Keeping personal information private online will help you
- protect yourself from social engineering attacks and identity theft,
- enhance personal security,
- avoid scams and financial loss,
- preserve personal and professional reputation,
- prevent extensive tracking, and
- comply with relevant regulations, to name but a few.
What Are the Best Ways to Protect Yourself Online?
Some of the best online protection practices include,
- creating unique, strong and complex passwords for your online accounts,
- applying two-factor authentication,
- keeping software updated,
- exercising caution when sharing personal information online,
- reviewing privacy settings,
- employing a VPN, and
- practicing safe browsing habits.
What Is Online Security?
Internet security refers to the practices, principles, and measures implemented to keep individuals, organizations, businesses, and their digital assets safe from cyber threats, unauthorized access, data breaches, and other Internet privacy issues in digital landscapes.