Some Windows users have recently complained about finding ransomware notes from the MHCADD malware on their PCs. MHCADD encrypts files on your computer and then asks you to buy the decryption service from its developers. In this post, we will look into how MHCADD works and what you can do to get rid of it.
Is MHCADD Malware?
The short answer to this is yes. MHCADD comes from a family of ransomware called Snatch. Its purpose is to encrypt the victim’s files, add its own extension to the filenames and create a ransom note. MHCADD adds the “.mhcadd” extension to your files: so, if you have a file named sth.jpg, it will become sth.jpg.mhcadd. The malware will also create the “HOW TO RESTORE YOUR FILES.TXT” text file in all of the folders where the affected files are located, which is basically a ransom note.
If you open the “HOW TO RESTORE YOUR FILES.TXT” file, you will find out that only the MHCADD developers can help you solve the problem. You will be asked to send an email to an email address listed in the file to get more details: the price of a decryption tool, how to initiate the process, etc. Unfortunately, the ransom file is not exactly wrong — in most cases, you won’t be able to decrypt MHCADD files using third-party software. However, listening to the ransom note and paying the price for decryption from the MHCADD developers is not a solution either. Typically, those who do pay for a decryption tool (or tools) do not receive it (or them) even after they’ve made the payment.
This is why it is generally not advised to trust MHCADD or pay the ransom. So, how to recover files encrypted by the MHCADD ransomware? Typically, the most certain way to recover your files is to restore them from a backup. An even better way is to prevent the ransomware from getting to your files in the first place — or, at least, to remove MHCADD before it can encrypt more files on your PC.
How Did MHCADD Get on Your PC?
In a lot of cases, MHCADD and other similar malware entities infect PCs via email. They can also sneak into your system through unreliable file or software download sources, third-party software updates, unofficial software activation tools, and more.
When it comes to emails, malware is often put in an attachment (popular formats include MS Office documents, PDFs, JavaScript files, executables like .exe files, archives like ZIP, RAR and so on, etc.) or a malicious download link. The emails often look important, urgent and official. Once you open the attachment or click the malicious download link, the malware gets installed on your PC.
As mentioned earlier, malware can also infect your system if you use unreliable download sources that distribute malware by disguising malicious files as legitimate. This typically happens on unofficial websites, free file hosting pages, peer-to-peer networks, and so on. Using third-party software updaters can also be risky: malware may disguise itself as updates and fixes for the programs that you have installed. Unofficial activation tools are quite similar. They are supposed to help you bypass licensed software activation (illegally) — however, instead of doing that, they install malware.
How to Keep Windows 10 Protected Against MHCADD
The best way to prevent your files from being encrypted by MHCADD is to make sure the malware never gets on your PC. This means that it’s best to take certain precautions:
- Only download the programs and files you need from official, reliable websites.
- Never open emails from unknown suspicious addresses and stay away from attachments and download links.
- Update the programs on your PC only by using the tools provided by official developers.
- Do not use illegal tools to update or activate any software.
Additionally, it is recommended to regularly scan your system for malware. Make sure to use antivirus software that you trust and that is up to date and can detect the latest malicious items out there. You can try using a program called Auslogics Anti-Malware.
Once installed, the program will run regular automatic scans of your entire system and locate even the rarest malware. If any threats are indeed detected, they will then be safely removed from your PC without causing any damage to the other elements of your system. The program is easy to set up and comes with a simple, user-friendly interface. Plus, the program is designed to run alongside other anti-malware software — so you should have no trouble running Auslogics Anti-Malware together with your other anti-virus tools.
How to Remove the MHCADD Ransomware
In the unfortunate case that the MHCADD ransomware has already made its way into your PC, you will surely want to get rid of it. There are several steps to this process, and it won’t be easy — but it is doable.
Here’s what you will need to do:
Step 1: Isolate the infected device
Step 2: Identify the ransomware infection
Step 3: Search for ransomware decryption tools
Step 4: Restore your files with data recovery tools
Step 5: Create data backups
Let’s start at the beginning.
Step 1: Isolate the Infected Device
Some types of ransomware encrypt files on external storage devices, infect them and then go on to spread over the entire local network. This is why it is essential to isolate the infected device as soon as you can.
If your computer is connected to the web via a wired connection, simply unplug the Ethernet cable from the motherboard. If your computer is connected to Wi-Fi, go to your PC settings and disconnect your computer from a wireless network. You can do all of this via the Control Panel:
- Go to the Control Panel.
![Open the Control Panel.]()
- Go to the search bar in the upper right corner of the page.
![Navigate to the search bar in the upper right corner.]()
- Type in “network and sharing center”.
![Enter “network and sharing center” into the search bar.]()
- In the upper left corner, select “Change adapter settings”.
![Navigate to “Change adapter settings” in the left pane.]()
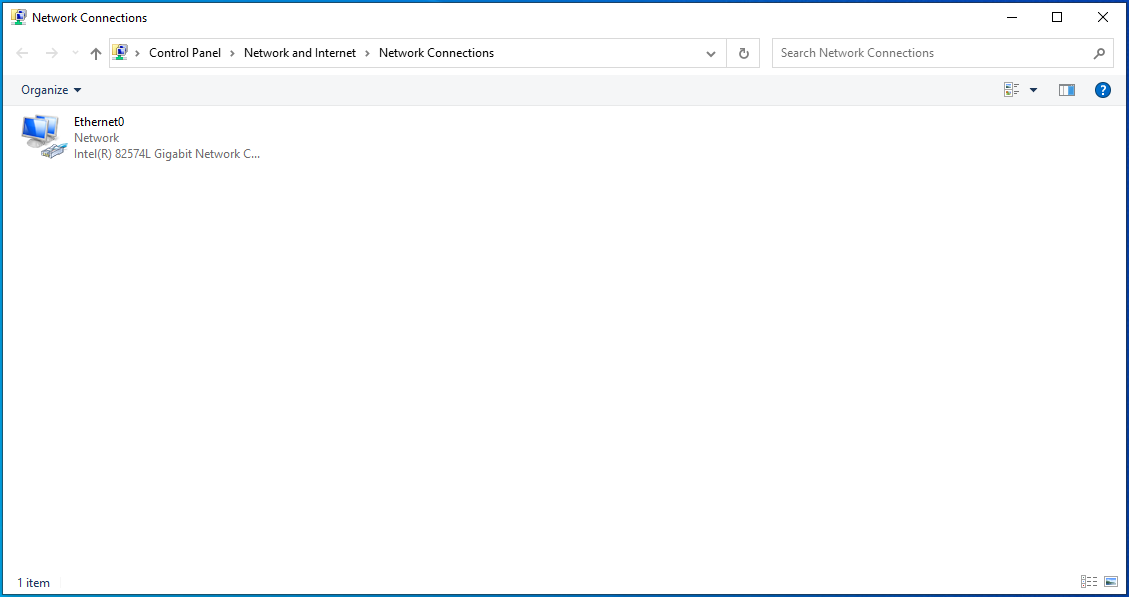
- Locate your connection point.
![Go to your connection point.]()
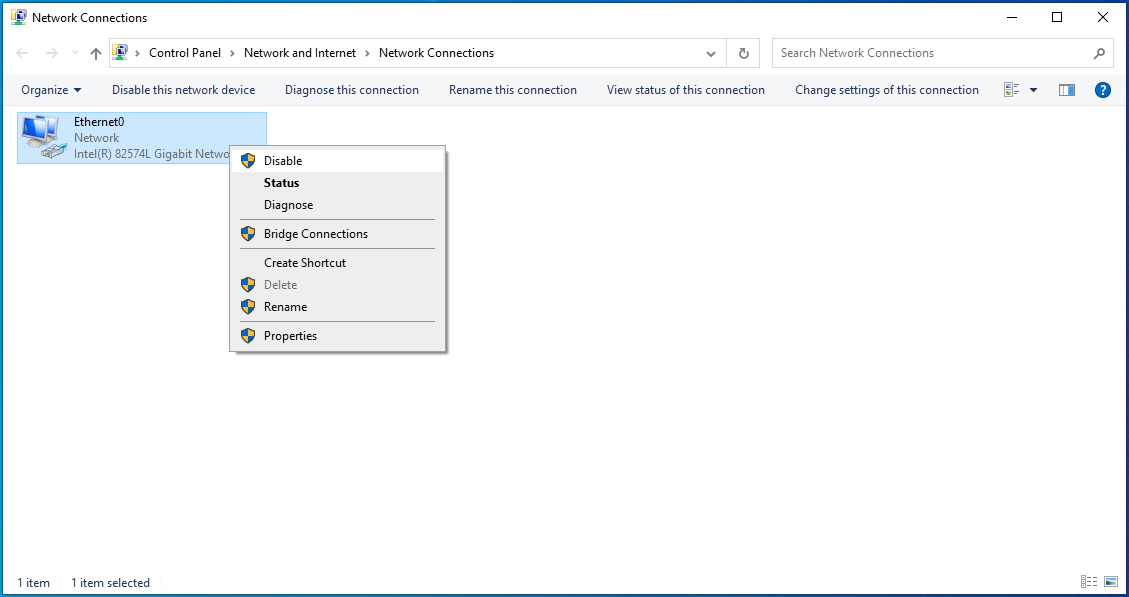
- Right-click it and select Disable.
![]()
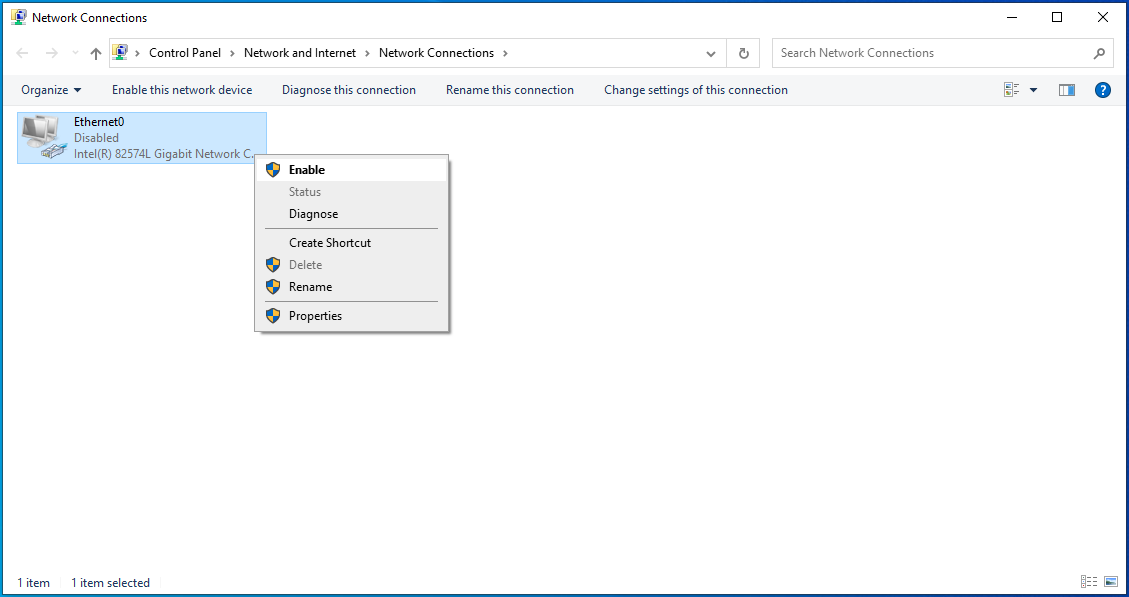
- This will disconnect your PC from the internet. When you are ready to go back online, simply repeat the steps above and select Enable.
![Right-click your connection and select Enable.]()
The next thing you will need to do is to unplug all storage devices. As we’ve already mentioned earlier, ransomware may encrypt data and infiltrate all storage devices that are currently connected to your PC. This is why you should disconnect all external hardware as soon as possible. Here’s how to do it:
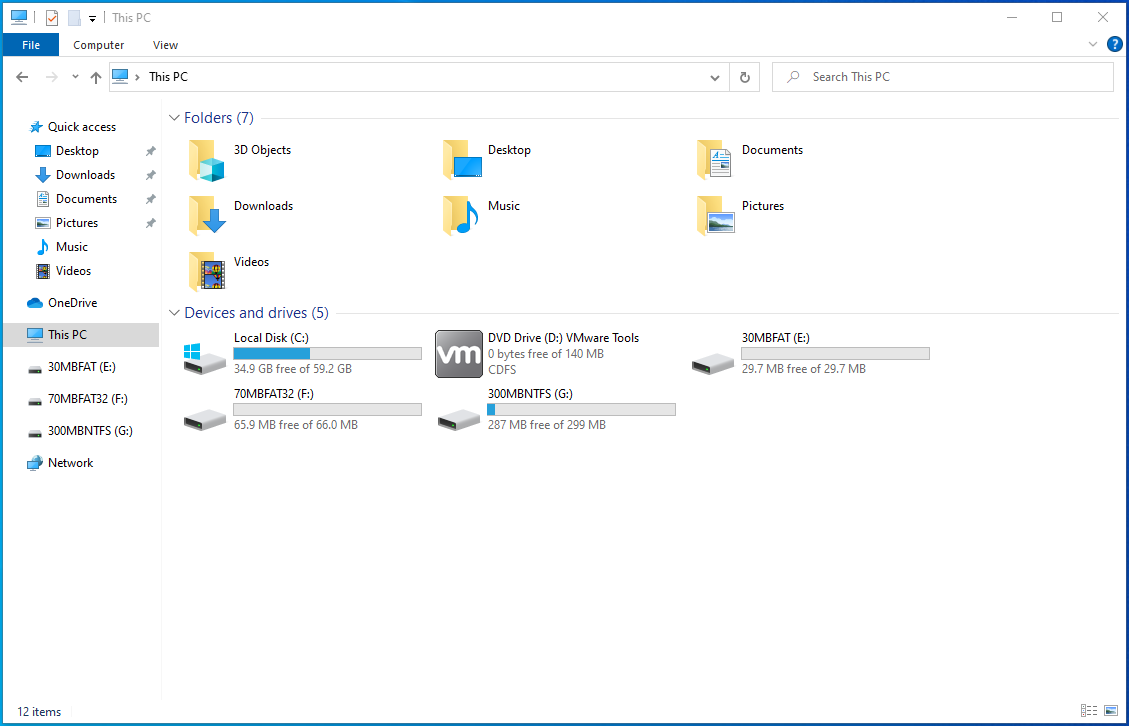
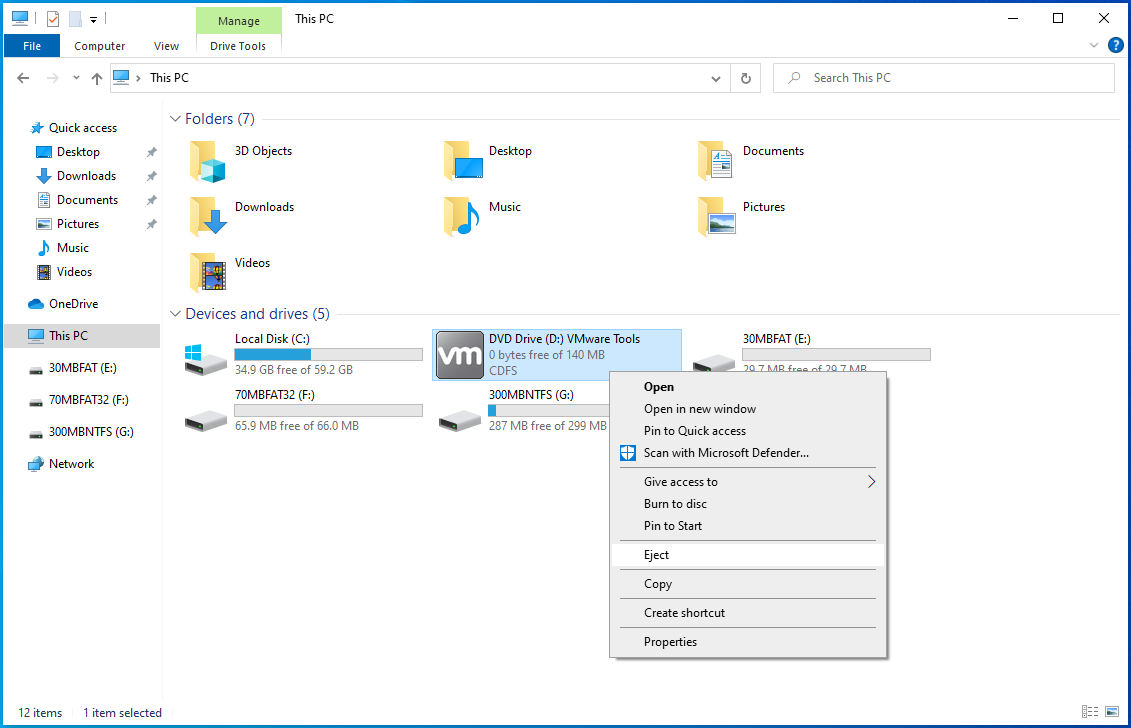
- Go to This PC.
![Open This PC.]()
- Right-click each connected device and select Eject.
![Right-click a connected device and click Eject.]()
Next, you will need to log out of all your cloud storage accounts. Certain types of ransomware are capable of hijacking the software that handles your data that is stored in the cloud. This makes your cloud storage vulnerable to being encrypted by ransomware as well. This is why it is better to log out of all your cloud storage accounts within browsers and other related software. You might also consider uninstalling your cloud management software (at least temporarily) until the infection has been properly handled.
Step 2: Identify the Ransomware Infection
Before you can take steps to get rid of the malware infecting your PC, you first need to identify it.
Most ransomware infections come with a file that includes a ransomware note. These messages are usually quite straightforward, and you may be able to identify what ransomware you are dealing with by simply looking at the name of the ransomware message.
However, in some cases, these names can be too generic. Plus, some infections may use the same ransomware note names. If you can’t clearly identify the ransomware by the name of its ransom note, it’s best to not risk it. If you attempt to decrypt your data using tools meant for different ransomware, you may end up causing permanent damage to your files.
Another thing you can do is check the file extension. Ransomware infections are often named by the extensions that they add to files. This usually works — unless the ransomware in question uses generic file extensions like “.encrypted”. In this case, you won’t be able to identify the type of malware this way.
One of the easiest ways to find out what type of malware you are dealing with is by using a specialized website that helps users identify malware threats. You will need to upload the ransomware message that you have received and one of the files that have been encrypted. The website will process the information, and if the ransomware has been identified successfully, you will receive details such as its name, decryption options, and so on.
If you don’t want to deal with a ransomware-identifying website, try running an online search with keywords like the ransom message title, file extension, provided contact emails, and so on. This can help you get more information on what you are dealing with.
Step 3: Search for Ransomware Decryption Tools
Encryption algorithms that are used by a large number of ransomware infections are quite sophisticated. In some cases, only their developers will be able to restore the encrypted files. This is because decryption requires a specific key that is created during the encryption process. If you don’t have the right key, restoring the data becomes simply impossible.
However, not all ransomware is created equal. Some ransomware infections may be poorly developed and contain quite a few loopholes: they may use identical encryption/decryption keys for their victims, store encryption keys locally, and so on. This is why you should always check for available decryption tools for any ransomware that infects your PC.
Finding the right decryption tool may be difficult, but it is not impossible. Plus, you can use one of the many online tools that can help you locate the right decryption software.
Step 4: Restore Your Files with Data Recovery Tools
In certain cases, you may be able to restore the encrypted data using a third-party tool. You can try running a search online and see if you can find suitable decrypting software.
Step 5: Create Data Backups
Finally, in order to avoid losing your data, it’s important to create backups for important files. Here’s what you can do to better protect your data.
It is recommended that you store your data in multiple partitions and not store important files in the same partition that contains your entire OS. If you ever have to face a situation when you need to format the disk on which your operating system is installed, you will end up losing all the data on that drive. This is why it is strongly advised that you create multiple partitions on your PC. This way, you can easily format a single partition without affecting the others. Managing partitions on your PC is not particularly complicated, and you can find all the related information on Microsoft’s documentation web page.
It is important to back up your data. The most reliable way of keeping your data safe is by using an external storage device and keeping it unplugged. Simply copy essential data to an external hard drive (flash drive, SSD, HDD, etc.), unplug it and keep it in a secure dry place away from direct sunlight and extreme temperatures.
Alternatively, you can use a cloud service or a remote server — for this, you will require a stable web connection. Unfortunately, cloud storage is vulnerable to security breaches, and you may not want to store highly sensitive information in the cloud.
And there you have it. We hope that the above information has been helpful in managing or preventing a potential MHCADD attack on your PC. Which of the solutions presented above have you found the most useful? Please share in the comments below.